From deliberate hacker attacks to accidental data loss, there are numerous perils that can befall your product documentation.
And since information is the most crucial asset a company can have, you have to know how to protect yours.
In this article, we’ll review the ways you can ensure the safety of your documents during all stages of production.
Fortunately, choosing the right software can take the brunt of the work, so we’ll see what features to look for in your documentation solution.
But first, let’s start with a safety measure that’s relatively easy to implement—cloud storage.
Host Your Documentation in the Cloud
If documentation safety and security are a priority in your business, then cloud storage is the right approach for you.
Let’s put it this way. What would happen to personal data if a person dropped their phone into the ocean?
There’s a 65% probability that absolutely nothing would happen, as that’s the percentage of people who consider the cloud to be their primary data storage.
But it’s not just that people trust the cloud to keep their pet photos safe. More and more businesses are also heavily relying on external cloud services to store sensitive data.
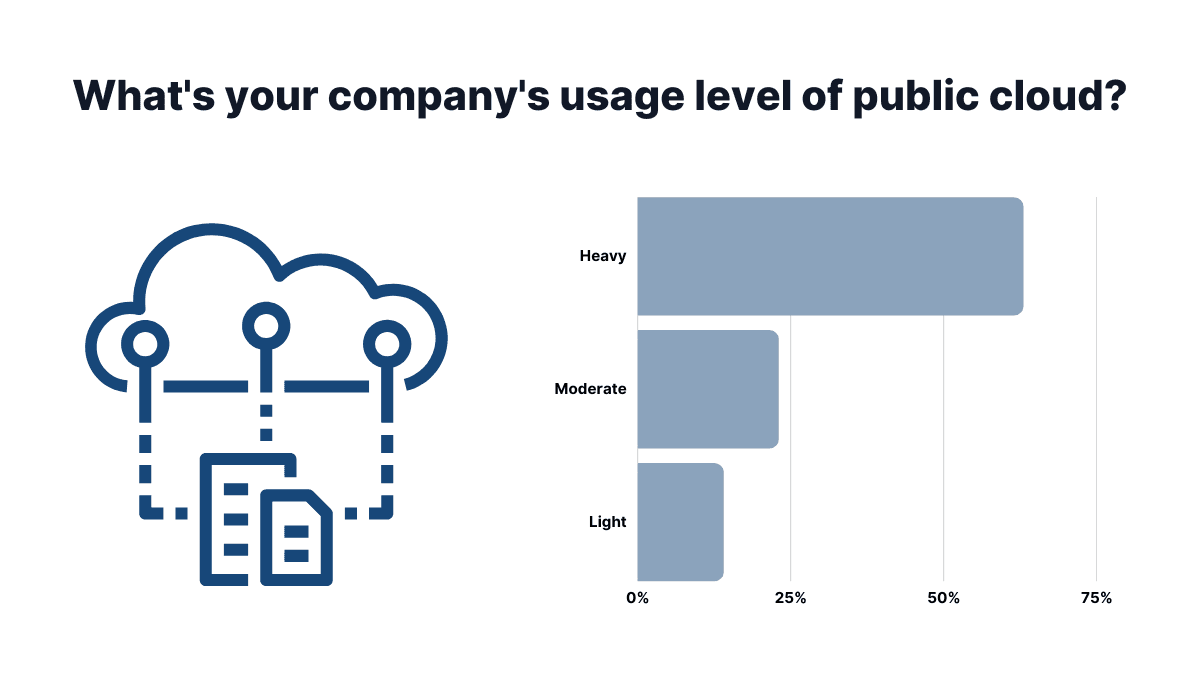
Illustration: Archbee / Data: Flexera
Seeing as you wouldn’t want to keep your docs only on fragile physical drives, it makes sense to join the cloud storage trend.
Another dominant reason why businesses choose cloud storage lies in the increased levels of security that are guaranteed by compliance with numerous standards.
So, when choosing your cloud storage provider, you should start by examining how it will ensure the security of your documents.
Bear in mind that this can also depend on the location of the servers. That’s why, for instance, Google Cloud sorts the security standards by region.
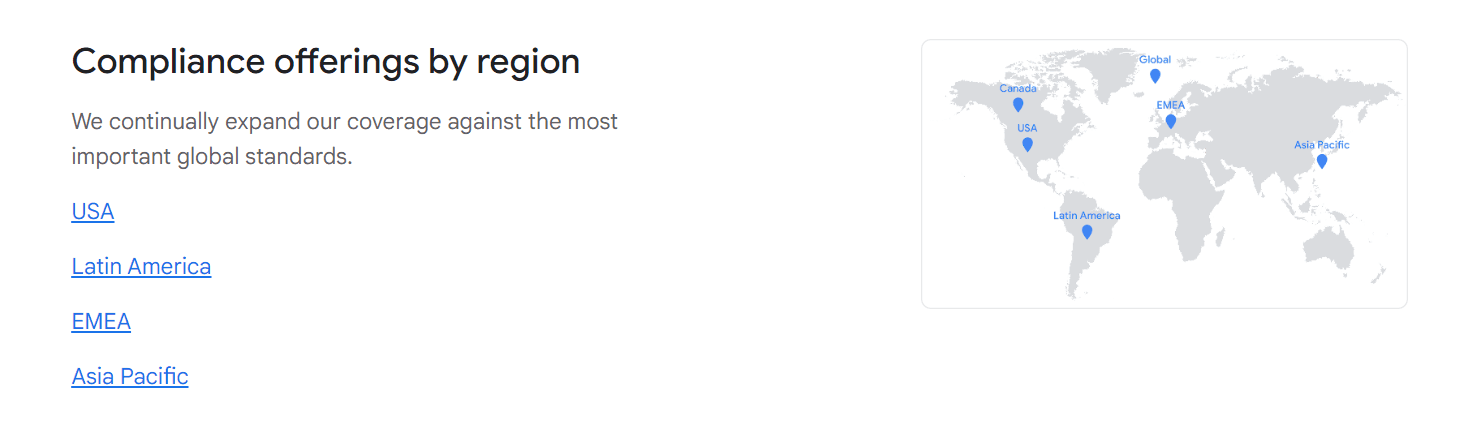
Source: Google Cloud
You’ll notice that many cloud providers boast the fact that some of their servers are located in Europe.
That’s because EU-based servers offer a safer environment for confidential data due to strict regulations such as GDPR.
So, if you clicked on the EMEA section in the Google Cloud regions, the GDPR would be one of the standards you’d see.

Source: Google Cloud
After you’ve selected the cloud provider that you trust based on its credentials, you still shouldn’t jump straight to payment and document migration.
Before signing the cloud storage contract, you should ensure that the following criteria are clarified:
- Data ownership
- Data retrieval after the contract ends
- Security and privacy policies
- Service levels
- Indemnity
- Limitations
At this point, you might think that selecting a cloud storage service and asking your dev and legal teams to review the contract seems like a lot of work.
Still, when you compare that to the amount of money you’d otherwise spend on expensive hardware, IT staff to maintain the storage, and energy costs, you’re likely to conclude that external cloud storage is a more reliable and convenient option.
Set Up Access Control
A vital factor of documentation safety and security is restricting who can view or use the files.
Because of that, your documentation tool should come with access control capabilities that let you select who to share your docs with.
Access control is a crucial aspect of document safety.
With more than seven hundred repositories dealing with the topic on GitHub, it’s clear that developers and their clients care about secure file sharing.
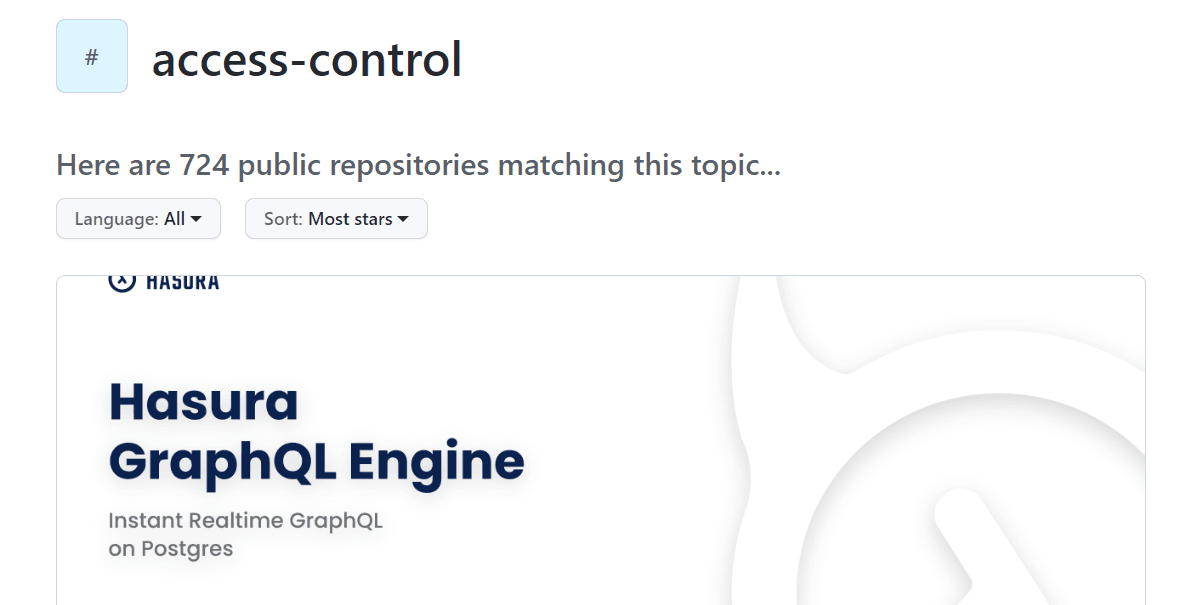
Source: GitHub
However, a DIY approach to security is rarely a good option. Instead, it’s better to use product documentation tools that have rigorous built-in access settings, such as Archbee.
Considering that security starts in-house, our product documentation platform allows you to control which teams or individuals get to read and edit the docs.
This feature is especially helpful because it’s not only the developers that need to access the documentation—you also have to equip the QA, marketing, sales, and support teams with files that allow them to carry out their tasks.
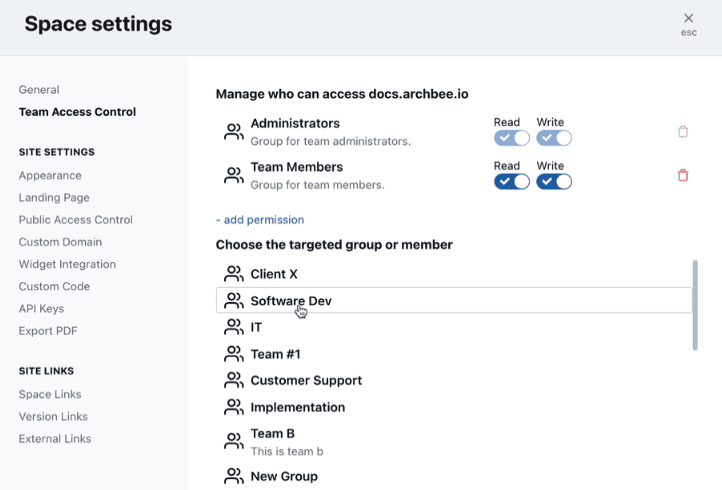
Source: Archbee
Still, the marketing teams don’t need access to sensitive code bases, so it’s better to limit their permissions to what’s truly necessary, such as user analytics and reports.
Besides internal knowledge bases, companies also frequently share product documentation with clients while the product is still in development, and that’s where security can get slippery unless you monitor it closely.
Seeing how important it is to ensure that confidential information doesn’t end up in the wrong hands, Archbee has implemented multiple levels of access control.
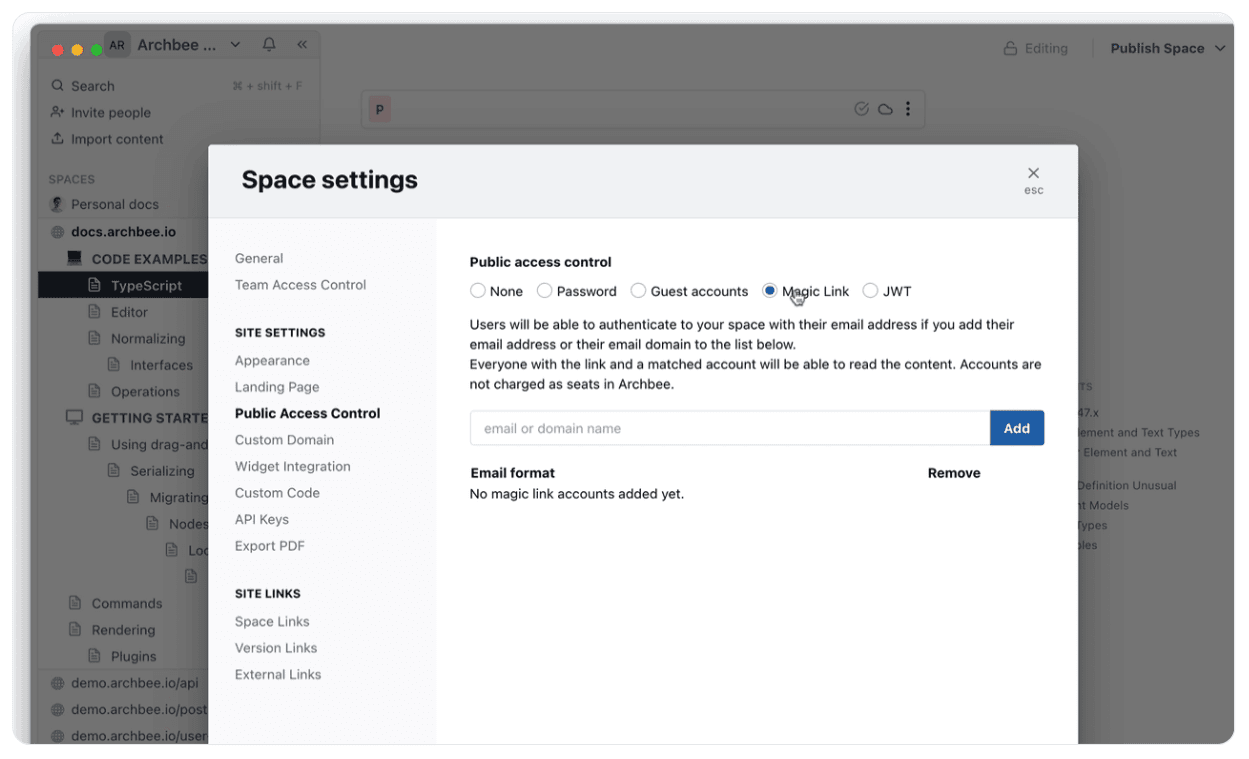
Source: Archbee
In addition to standard security practices, such as email and password combinations, Archbee lets you create guest accounts, magic links, and JWT keys that users can use for authentication.
That way, you can share information about the product’s progress with the clients without the risk of unauthorized parties accessing the content.
All in all, whichever platform you choose for development and documentation, make sure that it lets you control who can access the data, helping you preserve the highest security levels.
Encrypt Your Product Documentation
Encryption is a crucial cybersecurity tool, and no documentation platform is complete without it.
Looking at the history of cryptography will show you that encoding information, i.e., encryption, is hardly a new concept—it has been around since circa 600 BC, when Spartans used it to send secret messages.
Of course, the technology for preventing unauthorized access to information has come a long way since, and the use of encryption it’s still on the rise.
In fact, the number of companies that base their data security on encryption increases each year.
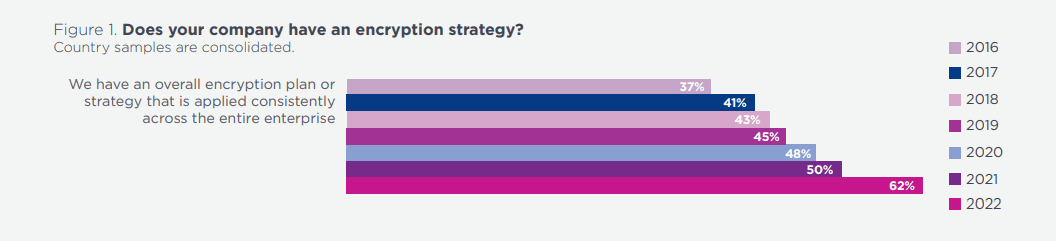
Source: Entrust
To ensure documentation safety, you can start by encrypting the hardware used by your teams.
That will protect your docs in case the equipment used to develop the product gets stolen.
Here’s what the device encryption procedure looks like on Windows.
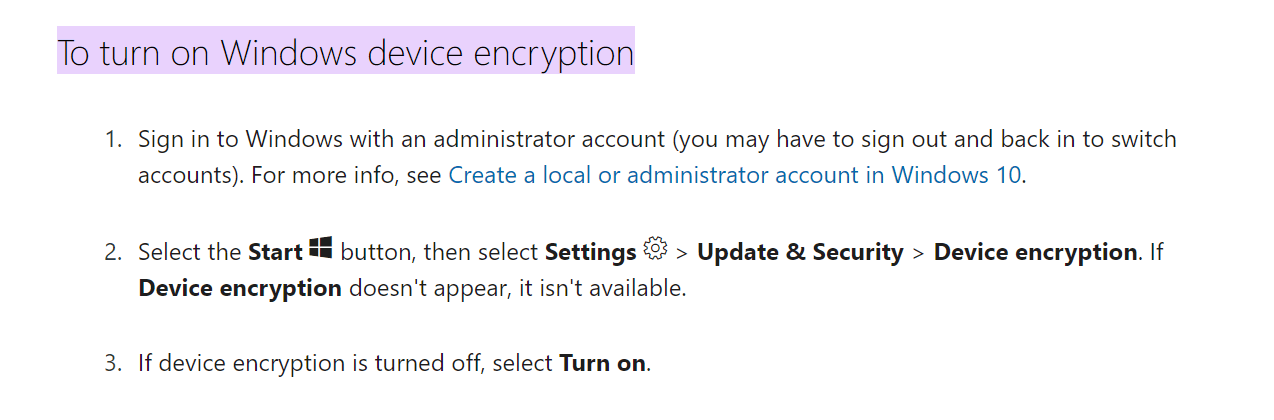
Source: Microsoft
However, encrypting the data stored online is even more important because that’s where the data is more likely to be compromised.
In the event that hackers gain access to your product documentation, you don’t want them to have it easy.
That’s why it’s best to encrypt the docs to make them unreadable to anyone without access permissions.
So, when deciding where to safely store your product documentation, you should check what encryption protocols and algorithms your solution uses.
Serious pieces of software will usually display what steps they are taking to maintain the clients’ security.
You can see Archbee’s own example below.
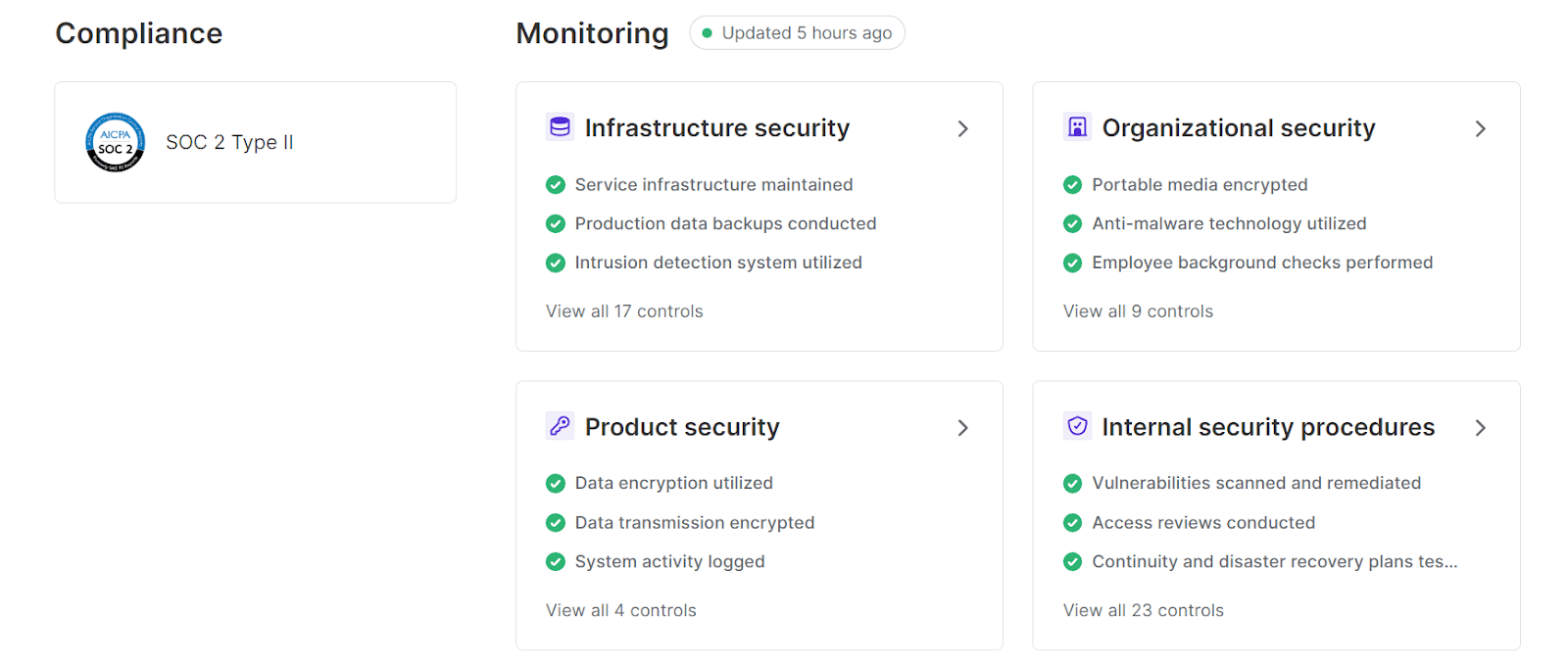
Source: Archbee
To sum up, you can never be too cautious about document security, and encryption is a must-have layer of protection.
So, before you even start writing the docs, make sure that they’re encrypted in every stage of the information journey, and that they can only be accessed with secure decryption keys.
Warn Employees About Phishing Emails
If you thought that emails from distant relatives from a faraway country asking for credit card details were a thing of the past, you’d be wrong.
Phishing is still very much present, although in a more sophisticated form, which makes it even more dangerous than before.
In fact, in 2022, phishing was the second most common cause of security breaches in companies, according to the IBM data breach report.
It was also extremely costly, averaging USD 4.91 million in breach costs.

Illustration: Archbee / Data: IBM
As we’ve mentioned, phishing emails aren’t necessarily as easy to spot as they used to be.
Because of that, it’s worth notifying all your employees to double-check all incoming emails before providing any details about the product documentation or other internal information.
Otherwise, they could fall for seemingly legitimate emails like the one shown below.
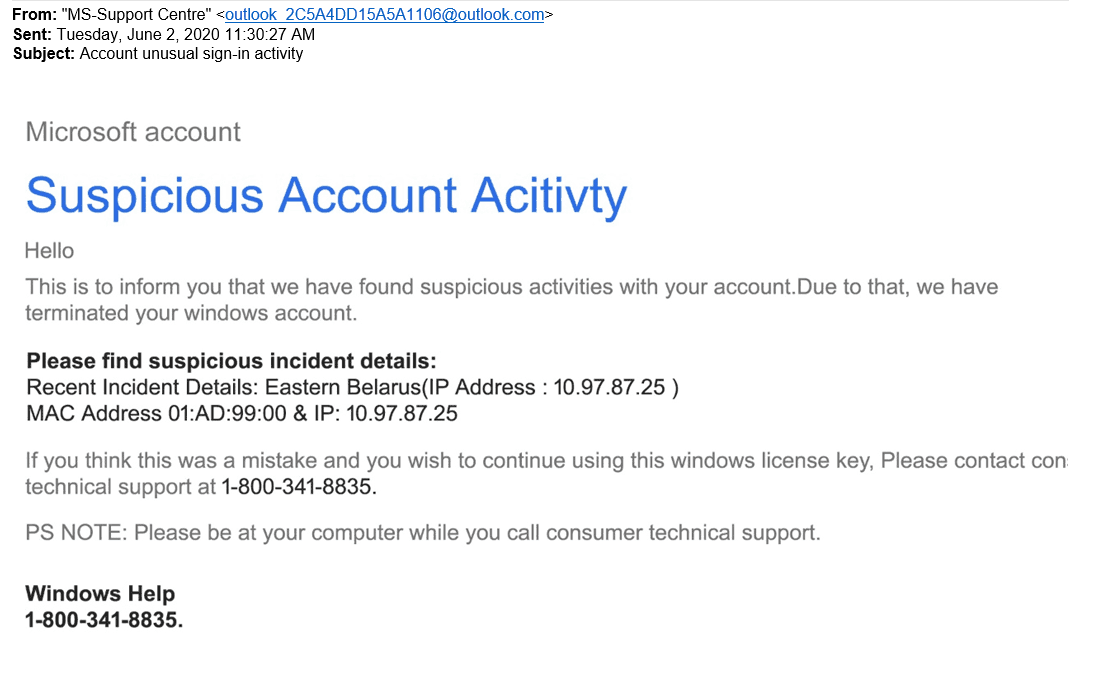
Source: Aura
As you can see, there are no glaring grammatical errors or design issues that could point to this email being fake.
However, a look at the sender’s email address shows that this is likely a fraudulent email—an official Microsoft email wouldn’t be sent from an @outlook domain.
In this case, the scammers have attempted to get the recipients to contact them and provide their personal data in the process of resolving a problem.
Since an untrained eye might overlook the signs of phishing emails, it might be a good idea to educate the employees on how to recognize that type of nefarious activity and stay alert, as advised by Jameson Lopp, a software engineer and online security professional.
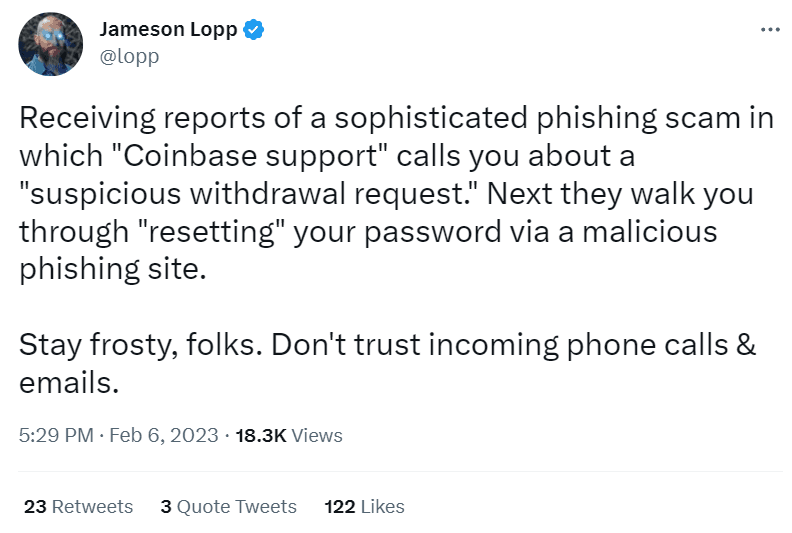
Source: Twitter
So, let’s list some common clues that your employees can use to identify phishing emails:
- The email is sent from a public email domain like Gmail, Yahoo, or Hotmail
- The domain name is spelled wrong
- Grammar and writing style are poor
- The sender is asking for login or payment credentials
While it’s best not to send confidential information via email, email still remains a necessary communication tool for development organizations.
Therefore, if your employees are planning to use emails, it would be wise to stress the importance of keeping the information safe and being mindful of phishing attempts.
Have Backups Ready if Needed
After you’ve proactively implemented the protective measures we’ve listed so far, it’s time to think about the worst-case scenario: what if something still goes wrong?
In that case, there’s no need for panic—frequent backups will save the day.
Perhaps the most famous example of a backup saving the project is the case of Toy Story 2.
There are numerous articles about the incident, but the story boils down to this: one Pixar employee deleted a large chunk of the movie.
Luckily, the supervising technical director had previously saved a copy on her own computer, accidentally keeping the entire project alive.
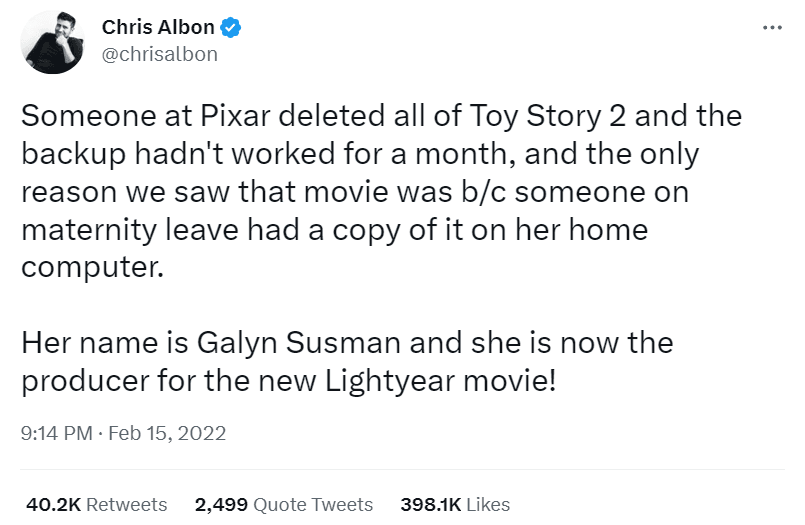
Source: Twitter
The story has since turned into a cautionary tale about the importance of backups.
For instance, Chris Albon, a machine learning and AI expert, has used it to warn his Twitter followers to implement and test backups for their important projects.
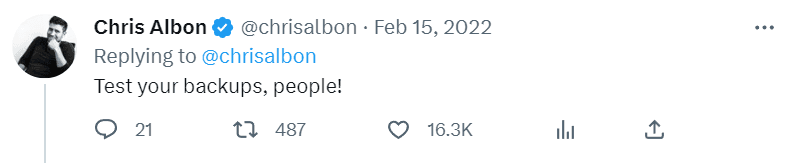
Source: Twitter
Rather than relying on employees manually copying product documentation onto hard drives, you should go for a simpler yet more effective protective measure.
We’re talking about selecting documentation tools that already have backup procedures in place.
When choosing your solution, you should consider where the data is stored.
You don’t want to put all your eggs in one basket, so, ideally, the data should be backed up to a cloud, an on-site server, and also an off-site data center.
The next factor to consider is the frequency of backups.
Weekly backups may not be sufficient, as even losing a week’s worth of work could cost a lot of money if you had to do it over. Instead, it’s better to look for daily backups.
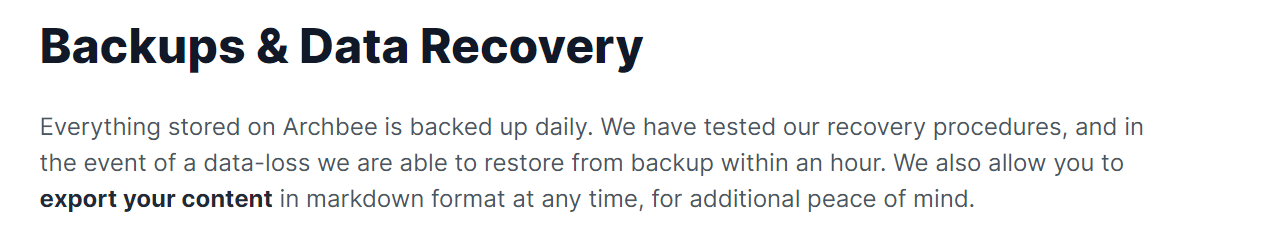
Source: Archbee
While documentation platforms that boast frequent backups and multiple storage locations might cost more, remind yourself that it’s a price you’re paying for your company’s resilience.
Even if data loss occurs, reputable platforms will be able to restore your documents so that you can continue developing your products unscathed.
Conclusion
Although no cloud or encryption service can claim to be 100% secure, combining several protective measures will get your product documentation as safe as it can be.
After all, product documentation is designed to be used for a long time, so it makes sense to invest in its protection.
We hope that this post has brought you some clarity when it comes to best document safety practices. And lastly, whatever you do, don’t use the word password for your password!
Frequently Asked Questions
Because the cloud gives you resilience, security, and collaboration you can’t get from individual devices or a single on‑prem server.
- Built‑in redundancy and durability: Data is replicated across multiple availability zones or data centers, protecting against device loss, theft, failures, and local disasters.
- Strong security by default: Encryption in transit and at rest, hardened infrastructure, DDoS protection, and continuous patching handled by the provider.
- Fine‑grained access and visibility: SSO, MFA, role‑based permissions, guest or time‑bound access, and audit logs so you always know who did what.
- Compliance and data residency: Certifications such as ISO 27001 and SOC 2, plus region selection (including EU) to support GDPR and similar regulations.
- Backup and recovery: Versioning, point‑in‑time restores, and geo‑redundant backups reduce the blast radius of mistakes or attacks.
- Scalability and collaboration: Teams anywhere can collaborate securely without capacity planning or hardware maintenance.
Net result: lower risk, faster and safer collaboration, and an easier path to meeting your security and compliance requirements.
